
SEC’s new rules on cybersecurity disclosure – What you need to know
 Intel made history as the first public company to disclose a cyber-related incident in its annual filing with the Securities and Exchange Commission (SEC). The disclosure was highlighted in a February 2010 Wall Street Journal article with the headline, “Intel Says It Was Target of Cyber Attack.” Interestingly, despite 30 other companies falling victim to the same cyberattack, not one of them provided a similar public disclosure.
Intel made history as the first public company to disclose a cyber-related incident in its annual filing with the Securities and Exchange Commission (SEC). The disclosure was highlighted in a February 2010 Wall Street Journal article with the headline, “Intel Says It Was Target of Cyber Attack.” Interestingly, despite 30 other companies falling victim to the same cyberattack, not one of them provided a similar public disclosure.
Since then, the corporate disclosures of cyberattacks and their financial impacts have varied just as widely in public reporting. The financial and investment community is grappling with an incomprehensible mix of reporting styles, levels of detail and transparency. Financial damages due to cyberattacks were no longer comparable by current public reporting standards – and the SEC took notice.
The new reporting rules
On September 5, 2023, the SEC adopted a new set of rules to ensure companies provide adequate and uniform disclosures of their cybersecurity incidents and management procedures. The SEC’s “Public Company Cybersecurity Disclosures; Final Rules” require your organization to both actively monitor and report on its cybersecurity programs and to detail any financial or other material impact resulting from a cyberattack.
Your reporting obligations
Beginning December 2023, specifics of your cybersecurity programs, along with the roles and oversight responsibilities of board members and executive leadership, must be reported in annual reports (10-K). Starting in June 2024 for “smaller reporting companies” (December 2023 for others), companies will be required to file 8-K updates on the material impact of a cyber breach – including realized and potential, estimated material impacts.
Determining cyber materiality is difficult
Materiality is an essential accounting concept. Yet calculating materiality can be complex, requiring professional judgment to determine estimates when hard numbers are unavailable.
Determining or even estimating cyber risk materiality is considerably more difficult. Calculations require analyzing significantly more external variables than financial materiality. Those variables change dramatically over time. The rapid growth of technology (both to protect and attack), the resulting vulnerabilities, new threat actors, and now the use of AI (again, to protect and attack) compound this challenge. Your material risk will change on a daily basis.
Automation is required to monitor, assess and analyze all these variables on a continual basis to obtain accurate and timely determinations of material impact associated with every exploitable risk.
BPM can help
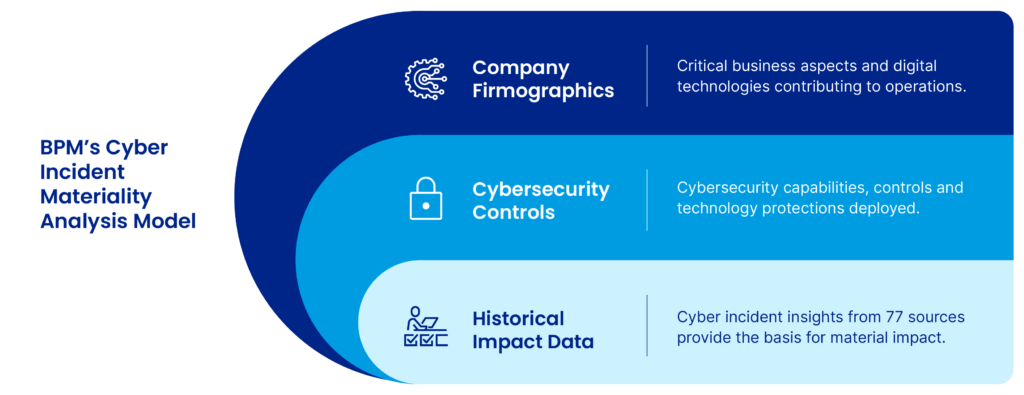
In response to this pressing challenge, BPM launched an innovative service designed to assist clients in determining the material impact of cyber breaches. Our service leverages a cyber risk analytics model comprised of multiple actuarial calculations. The model determines the material impact of multiple threat scenarios – by risk category – specific to your organization’s unique demographics, established protections and risk management controls. Results are delivered to your executives and board members in a set of easily digestible dashboards to instantly assess risk exposure for any region, vertical, division or asset.
BPM recognizes the challenge facing our clients in complying with the SEC regulations. If you have questions or concerns about meeting the new cybersecurity filing requirements, please contact BPM today.




