INSIGHT
Data Privacy is a rapidly growing focal point in information security. According to Google search criteria, the top 32% of queried security topics within the last quarter of 2019 involved data privacy, data breaches and data sensitivity. This has been a growing trend since the release and implementation of the General Data Protection Regulation (GDPR) in the European Union. Now, with the new regulations and law for the California Consumer Privacy Act (CCPA) and the Oregon Consumer Information Protection Act (OCIPA), consumers and businesses have become increasingly aware of the need to ensure the security of Personally Identifiable Information (PII). California and Oregon have taken steps to create tailored regulations for their residents, and now organizations doing business in or with these states this year must consider the impact of compliance across multiple geographical areas.
What is PII and how is it sold?
The expansion of the definition of PII is a central focal point of the increased data privacy regulations. Each body has different classifications for what is considered PII, and it is crucial to ensure your organization is adhering to the strictest definition for your client base. Figure 1 outlines the considerations for personal data under the existing and incoming regulations.
Figure 1
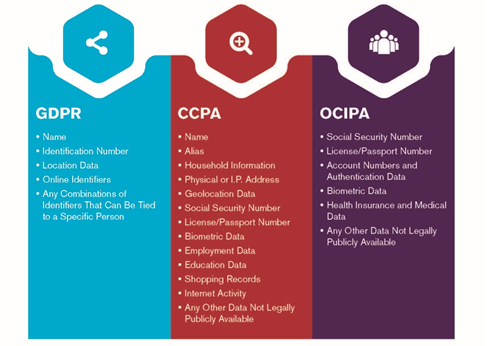
There are assumptions that the selling of PII is limited to the direct, for-profit selling of consumer data. This is, however, not the entire scope of what it means to sell personal data. If your organization shares personal data for any monetary purpose, including marketing, you are engaged in selling personal data. You must take steps to ensure reasonable care is taken to protect that data, and that safeguards are in place that meet the requirements of all applicable data privacy laws.
What are my customers’ rights?
Individuals now have greater control over the collection and use of their personal data. Upon initial collection, the full intended use must be spelled out in an easily understandable manner, and any collected information may only be used that declared purpose. This creates an added layer of oversight difficultly for organizations, as they must be able to map every piece of collected data to its ultimate usage and provide proof of consent for that usage. Additionally, consumers must have ready access to company contact information in order to reach out for all matters regarding their personal data. It’s your organization’s responsibility to have prominent, publicly posted contact information with a path to a Data Privacy Officer who can assist individuals in:
- Accessing their personal information;
- Updating their personal information;
- Removing their personal information;
- Opting out of marketing materials; and
- Opting out of selling their data.
Under all regulations, organizations may retain sanitized (i.e., anonymized) information that cannot be directly linked to an individual. These pieces of information can help analyze historical data without violating data privacy regulations.
What about my vendors?
The requirements for data privacy security extend out from your organization and into all the third-party vendors you use in your day-to-day operations. These could be providers of a Human Resources Information System (HRIS), a payroll processor, an accounts payable or accounts receivable service provider, a SaaS platform, a cloud service or provider and a multitude of other third parties. Bottom line – if your customer or employee data is shared with a third party, it’s your responsibility to ensure the third party complies with all applicable data privacy regulations. To protect your organization, all Service Level Agreements (SLAs) should be updated to reflect your specific data privacy requirements, and how your organization expects your customers’ data to be handled.
What about our liability insurance? Won’t that cover us?
Liability insurance may not be enough protection, depending on your policy or the size of your company’s client assets. The value of the policy depends on the predicted full-support needs of your client base after the breach. By assets, we also mean the actual data your company holds for its clients. If you are a credit card processor, storage entity, marketing firm, insurance office, medical complex or the local Jiffy Lube, you probably store, transmit or share data. If it becomes unsecured, unprotected, unencrypted and your company is not prepared, it could be catastrophic to your business or company. Most small business owners haven’t thought about the insurance level or the ramifications of a data breach, yet 75% come from small businesses.
Sometimes, the common laptop or business cellphone loss or theft becomes a data privacy issue. If we cannot definitively establish what data was on that device, or know if the device was fully encrypted, or if we cannot restore that data with viable backups, we risk a compromising data breach.
How can we protect ourselves?
There are several layers to ensuring your organization is doing everything it can to comply with data privacy regulations.
- Create a Data Privacy Policy and associated Procedures that:
- Identify what you classify as PII within your organization;
- Define the necessary usage of PII within your organization; and
- Describe the data flow process, including collection, usage, retention, and destruction.
- Create and deliver Security Awareness Training that specifically addresses the criticality of data privacy to all employees upon hire and annually.
- Review existing contracts and SLAs to ensure all compliance measures are in place.
- Consider the coverages and limitations of your organizations liability insurance.
BPM’s IT Security Advisory practice leaders bring with them decades of in-house IT and consulting experience, and are ready to tackle your organization’s data privacy compliance needs in 2020. Contact our IT Security & Compliance team today and start the New Year off on the safer foot.
Start the conversation
Looking for a team who understands where you’re headed and how to help you get there? Whether you’re building something new, managing growth or preserving success, let’s talk.