INSIGHT
What does digital transformation mean for your security posture
March 21, 2022
Managing supply-chain risk is an integral part of successful digital transformation
In a constantly changing technology landscape, forward-looking organizations continually embrace a succession of digital transformations. Digital transformations – whether comprehensive automation of core organizational workflow, cloud migrations, or adopting new ways of analyzing data – often improve security. Some business leaders are skeptical about storing documents on the cloud. They shouldn’t be. But digital transformations alter the organization’s attack surface, and those changes need to be assessed for any security holes. The good news is that companies undergoing digital transformations can adopt practices to manage risk related to their digital transformation efforts.
One of the biggest cybersecurity challenges that organizations face with their digital transformations is managing their vendors and making sure that their own systems aren’t at risk because of flaws in third-party systems. There has been a tectonic shift in vendor management and third-party risks in the last few years. Until recently, most breaches were caused by coding flaws that hackers could exploit, social engineering attacks, misconfiguration breaches, and credential compromises. But public perception of breach origins changed with the SolarWinds attack. Unlike many digital attacks, which are quick “smash and dash” operations, the SolarWinds breach resulted from a well-funded long con, exploiting an application that demanded the highest levels of access and privilege on client networks. It changed the landscape of IT security and rewrote the rules on how organizations needed to protect themselves and manage vendor risk.
More recently, the Log4j vulnerability has proven to be just as destructive and damaging and has made it easy for just about anyone to exploit sensitive and secret information. These vendor supply chain attacks have shed light on the complex dependencies organizations face when adopting new applications or migrating services to the cloud.
Vendor supply chain vulnerabilities such as SolarWinds and Log4j illustrate the inherent difficulties in knowing where weaknesses lurk. For example, no organization can hope to find every instance of Log4j in every third-party application they own or use. Those vendors don’t know every instance of Log4j usage by all the open-source components that went into their product, and so on. The potential number of places where vulnerable code can be lurking in a modern application is a tangled web of re-usages and inter-dependencies.
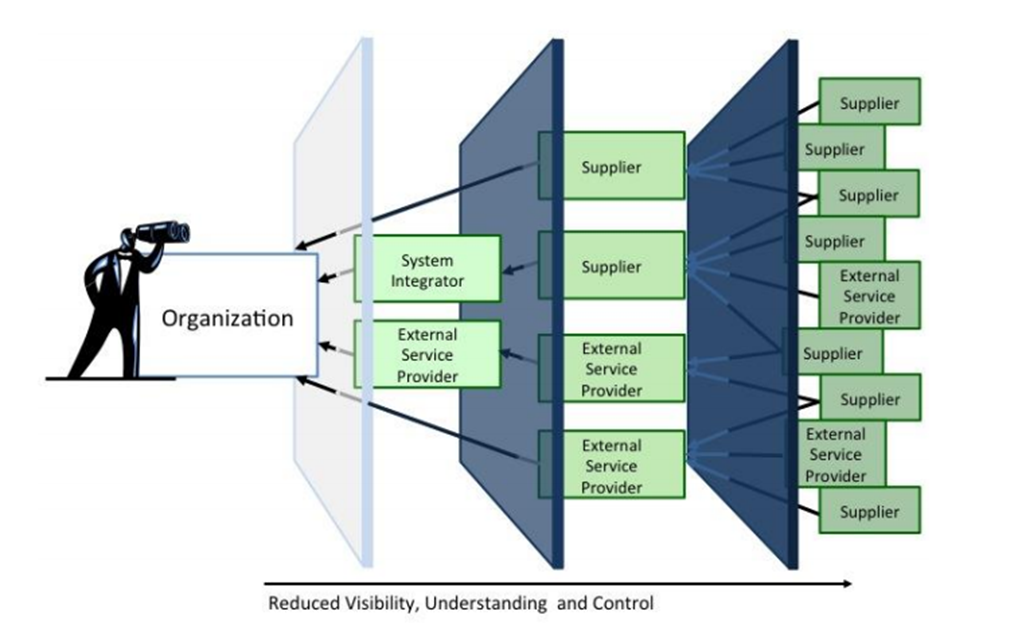
Source: Supply Chain Risk Management Practices for Federal Information Systems and Organizations
What can be done
Unfortunately, there aren’t a lot of easy answers to this dilemma, but that doesn’t mean that organizations should simply throw up their hands in despair. There are both internal and third-party vendor due diligence processes that organizations can adopt to manage this growing risk.
Vendor due diligence is now more important than ever because any organization that is considering third-party solutions needs to know if a technology provider displays a culture of cybersecurity. In simple terms, organizations need to know that their technology partners take data confidentiality, integrity, and availability seriously and will act aggressively to prevent, and respond to, security incidents and breaches. Ask questions, demand evidence of due diligence, and hold vendors’ feet to the fire around cybersecurity – especially before signing the purchase agreement.
There are also key internal steps that all organizations can take to begin adopting a zero-trust model when it comes to all applications, systems, and migrations. Rigorously implement the concept of least privilege, e.g., question when the vendor claims their product needs administrative-level privileges. Also, organizations must collectively up their game around log reviews and alerting. If we assume that we can’t find every instance of Log4j, then we should be vigilantly watching for anomalous behaviors and artifacts that Log4j breaches generate. And we need to build security programs based on a standard, e.g., NIST, that ensures we’re covering every aspect we’re supposed to be covering with our information security efforts.
These combined approaches to managing supply chain risk can significantly reduce cyber-risk resulting from third party security dependencies. For more information about how BPM can help you radically improve the cybersecurity of your organization, please reach out today.
Start the conversation
Looking for a team who understands where you’re headed and how to help you get there? Whether you’re building something new, managing growth or preserving success, let’s talk.